IoT pentesting is a new domain that have entered in penetration testing. With the growing risk of IoT security, attack on various IoT devices, often pentesters are asked by various companies to pentest or check their systems. But the problem is that most security service providers don’t yet have IoT specialist for testing, it is usually done by regular security team. In this article we will try to see what exactly is IoT penetration testing.
The difficulty level and the steps to perform the testing is almost similar to that of regular testing but if you are discovering flaws via analyzing firmware or via analyzing wireless communications then its going to be difficult.
The benefits to pen testing Iot include strengthening device security, protecting against unauthorized usage, avoiding Elevation of Privileges, Lower reducing the risk of compromise, better user and data privacy, and setting strong Encryption to avoid man-in-the-middle (MTM) attacks.
Most of the currenct research focus on vulnerabilities on the device but it is important to have a look at other areas too. Areas pentesters needs to focus
- The devices themselves
- The operating system that runs on the devices
- The software on the devices
- The mobile application
- The servers themselves
- The build on the servers
Basic IoT Architecture
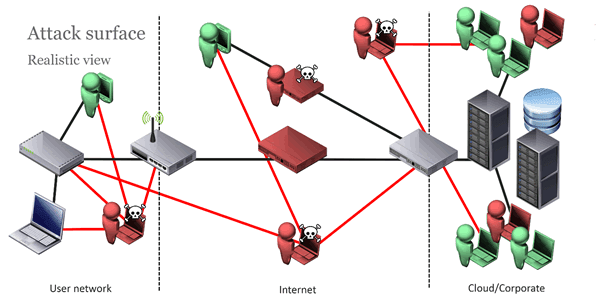
An attacker gets many ways to breach an IOT system as its architecture compromises a number of elemets that becomes potential hacker’s target
IoT architecture consists of the following components :
Things: Smart devices equipped with sensors and actuators.
IoT field Gateways: Border elements that provide connectivity between things and the cloud part of an IoT solution.
Cloud gateways: Components facilitating data compression and transmission between the gateways and cloud servers.
Streaming data processor: An element ensuring a smooth transition of input data to a big data warehouse and control applications.
Data storage: Consists of a data lake (stores unprocessed data in the form of “streams”) and a big data warehouse (stores filtered and structured data, as well as context information about smart devices, sensors, commands from control applications).
Data analytics: A unit that uses information from the big data warehouse to establish data patterns and gain meaningful insights.
Machine learning: Generates and regularly updates models based on the historical data accumulated in a big data warehouse which is used by control applications.
Control applications: Components that send automatic commands and alerts to actuators.
Client-server system: Consists of a user business logic component (the server side), a mobile application and a web application (the client side).
Penetration testing is executed on the following elements of things:
- UART, JTAG, SWD ports. Exposed ports allow a pentester to get root access, view and modify sensitive data.
- Flash memory chips to detect a possibility to dump firmware.
- Bus sniffing. Hackers may sniff clear text data between components and get access to sensitive information.
Book to follow
IoT is interesting and yet a hard topic to follow. Here is a book which i recommend which you can use to learn more about IoT . here is a book by popular security researcher Aditya Gupta who is an expert in Iot Pentesting


![PoC Code published for instant Blue Screen of Death [ Flaw unfixed ]](https://hackatrick.com/wp-content/themes/mts_writer/images/nothumb-writer-related.png)